2018 started off with a big bang for the IT industry because the newly-discovered CPU flaws, Meltdown and Spectre, could affect almost any processors in computers and mobile devices made in the past 20 years.
This is especially scary since these flaws can be exploited to gain access to encryption keys, passwords and other sensitive information by breaking the critical operating system memory defenses and then bypassing fundamental isolation layers — including those used by virtualization and container technologies!
Flaws like these quickly become part of a hacker’s standard toolkit and it’s only a question of time when these get exploited by ransomware attacks or in other malicious scenarios. Now Microsoft and other OS and CPU manufacturers are scrambling to create patches to fix the flaws — which in turn means IT has to hustle to deploy these patches as soon as possible.

Negligent Or Careless Employees, BYOD Are The Biggest Threat To Endpoint Security
Did you know that an alarming 90% of organizations recently said in a survey that they feel they do not currently have the capability to stop employees from using their personal mobile devices to access enterprise systems?
This is rather shocking given the fact that 81% of IT pros consider negligent or careless employees not following security policies as the greatest threat to endpoint security — not to mention all the others who are intimidated by the increasing (insecure) number of mobile devices and personal devices (BYOD) being used for work:
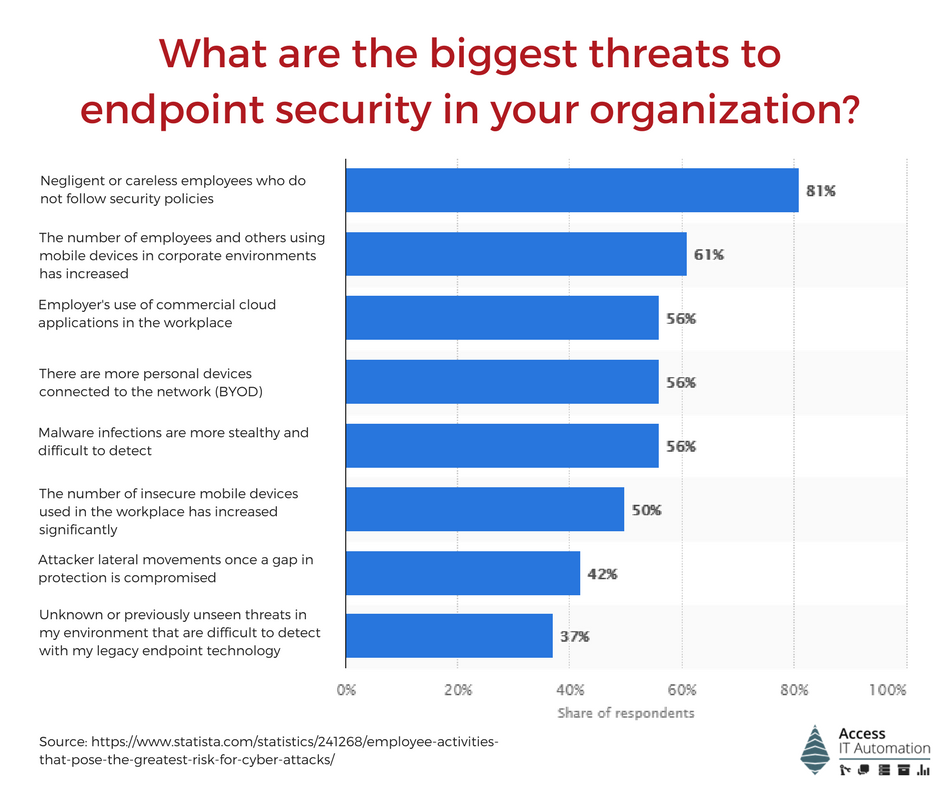
In addition to that, there are physical threats such as laptops being stolen or terminated employees downloading corporate data to personal devices before handing in their computer. However, not being able to control and manage your end points is putting your organization at risk.
Thankfully, you can leverage the power of IT automation to immediately tighten your endpoint security by:
- Identifying devices that hold security vulnerabilities and quickly run patches to fix those
- Remotely disable lost, stolen, or endangered devices
- Notify your end users of a potential vulnerability and give them guidance on how to proceed
- Better enforce BYOD security policies
- Detect and prevent possible security threats
… and much more. Let’s have a closer look at each scenario:
Use IT Automation As A Fix Engine To Identify And Patch Security Vulnerabilities
Therefore, you have to be able to quickly identify potentially vulnerable devices, lock them down, and patch every machine. However, in the Meltdown case, Microsoft’s patch seems to have compatibility issues with already installed antivirus software and executing the incompatible patch currently results in boot failure.
If you have an endpoint management tool like Agent installed on every device, you can not only identify all vulnerable computers within seconds but also cross-check if they run one of the incompatible Antivirus programs. Then you can execute a Powershell script and deploy it globally across all applicable devices with a click of a button.
Use IT Automation To Remotely Disable Devices
In addition to cyber security vulnerabilities, there are also other possible scenarios that would put sensitive data at risk. For example, you might want to remotely disable corporate devices used by a former employee before he or she has a chance to download company data onto private devices or wipe data from lost or stolen devices. In case of a physical threat, you might need to shut down specific device types or disable devices in a particular building, office location, or line of business unit.
Notify Affected Users Of A Detected Vulnerability
In addition to being able to send the commands remotely to execute a fix a vulnerability, you might also want to notify users and make them aware of a certain vulnerability or expected issues. With Access Agent, select end users will receive real-time notifications with a click of a button. This communication could include more in-depth information on the threat itself, warning signs to look out for, and what to do if you suspect you have encountered it.
Enforce BYOD Security Policies
When it comes to IT and cyber security, “better safe than sorry” is the mantra to live by. However, many IT folks feel that the increasing number of unsecured mobile devices or personal devices used for work purposes as part of a Bring-Your-Own-Device (BYOD) work environment expose their organizations to cyber security threats.
And rightfully so! In a study by Ovum, 79% of employees in high-growth markets say they prefer BYOD. However, 17.7% do so without their employer’s IT department knowing about it. Oftentimes, if the IT department is aware of employees bringing personal devices to work, they feel their hands are tied. What good is a strict security policy if you cannot enforce it?
Well, with IT automation you can. By installing Agent on every device used within corporate walls, you have more control over what your co-workers can and cannot do. For example, you can restrict printer usage or outgoing emails. Once those policies are formally defined, they can be written and stored within a security policy framework within Access Agent and executed when needed or in the background.
Detect & Prevent Possible Security Issues
One very common security flaw created by negligent or careless employees is using an unencrypted USB device or even connecting local hard drives. In this scenario, you could use Access Agent to detect an unsecure device being plugged in and immediately restrict the use of that device so no one could gain access to data or copy files there. You would simply create and run a script that checks drives. If an unsecured device has been found, you can inform the user or even go as far as deleting files or moving files to network drives.
Conclusion
Unfortunately, data breaches, malware and ransomware attacks and other security threats aren’t the exception anymore. It’s only a question of time when your organization will be affected. Thankfully, there are effective ways that IT automation can be deployed in a matter of minutes to not only patch an occurring issue, but also ringfence a problem before it spreads. In addition, IT automation tools like Access Agent allow IT admins to proactively build a repository of fix scripts to be applied in all kinds of scenarios.
To close, I want to challenge you to think of your three most impactful security challenges that your organization is facing right now. Then schedule a meeting with me and I will attempt to create a plan to fix it using Agent! Let’s see if I can do it!